
CrowdStrike Falcon Cloud Workload Protection
Breach prevention for cloud workloads and containers
Protecting Workloads Across All Data Centers
The CrowdStrike Falcon platform simply and effectively protects all workloads, including containers, running in all environments, from public and private clouds to on-premises and hybrid data centers.
cloud workload protection across all environments
CrowdStrike Falcon® Cloud Workload Protection provides comprehensive breach protection across private, public, hybrid and multi-cloud environments - all delivered via the lightweight Falcon agent and managed by the CrowdStrike® cloudnative platform. The Falcon platform allows customers to rapidly adopt and secure technology across any workload.
Key Benefits of Choosing Falcon To Protect Your Data Center

BETTER PROTECTION
The CrowdStrike Falcon® platform delivers prevention, detection and response capabilities to ensure stealthy attacks — and breaches — are stopped.

VISIBILITY
It provides end-to-end visibility - from endpoints to servers, workloads and containers - so you can detect attacks that involve multiple types of workloads and move across different types of environments.

REDUCED COMPLEXITY
It unifies security across all data centers - on-premises, cloud, multi-cloud and hybrid - with one platform and one console.
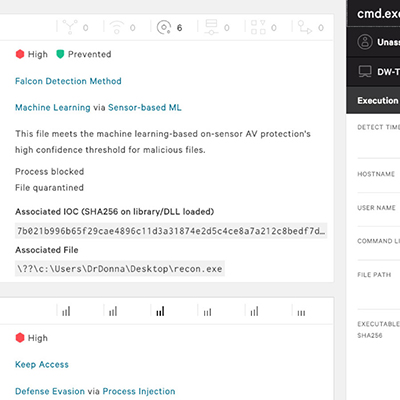
Prevention
- A powerful array of technologies - from machine learning and artificial intelligence (AI) to indicators of attack (IOAs) - detects and prevents all types of intrusions, including ransomware and stealthy nation-state attacks
- Threat-intelligence-based prevention capabilities block known malicious activities
- Powerful response actions allow you to contain and remotely remediate systems
- Managed threat hunting 24/7 ensures that stealthy attacks don't go undetected and that breaches are stopped
End-to-End Visibility
- See and hunt threats with centralized, real-time visibility across workloads, regardless of their nature or their location
- Identify unmanaged assets and rogue instances so you can close the gaps in your IT operations
- Find vulnerabilities before they lead to a breach
- See the current threat level of the organization in real time and how it changes over time
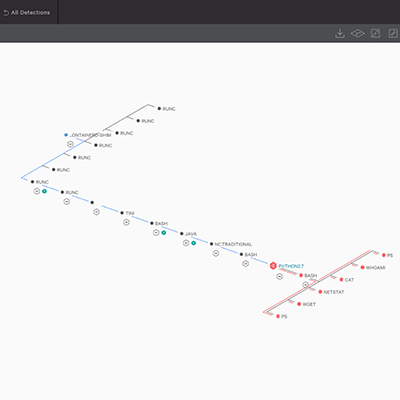
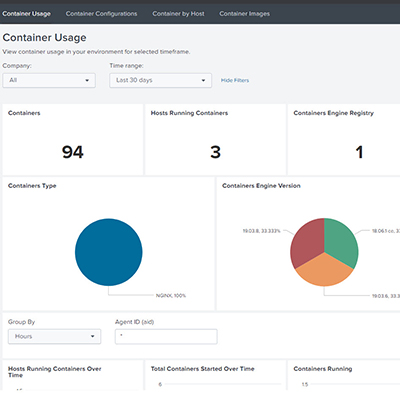
EDR for Containers, Runtime Protection and Discovery
- Endpoint detection and response (EDR) provides visibility for container activity, enabling security teams to track down threats to the individual container. It also supports container-specific investigations
- Runtime protection engages the powerful CrowdStrike® Falcon prevention and detection technologies to defend containers against active attacks
- Immediate container discovery and visibility allow you to easily view container information including usage and trends, container detail by host, container images used and configuration
- Protection that does not sacrifice performance, matching the speed of DevOps and adapting to the dynamic scalability of containers in real time
Speed and Simplicity
- One unified console provides central visibility and control over cloud workloads regardless of location
- The single, lightweight Falcon agent is easy to deploy, scales in minutes and has little impact on the host and zero impact on runtime performance. It secures host and containers without installing any additional containers for security
- A broad set of easy-to-use APIs provides interoperability with other security platforms and tools
- The cloud-native platform operates without constant signature updates, scan storms, complex integrations or on-premises equipment
Key Capabilities
Visibility into Cloud Workloads
Comprehensive visibility into cloud workload events and instance metadata enables detection, response, and proactive threat hunting and investigation, ensuring that potentially malicious activities don't go unnoticed.
- Gathers metadata at the instance level to easily identify owners of assets involved in an alert
- Groups hosts by account ID, allowing for quick and easy visualization and identification of assets per owner
- Automatically detects and intelligently prioritizes suspicious and malicious activity
- Continuously monitors events to provide visibility into workload activities, including activities running inside containers; a full set of enriched data and event details allows investigations against ephemeral and decommissioned workloads
- Delivers proactive threat hunting across all workloads and endpoints from the same console
- Detects and investigates attacks that span multiple environments and different types of workloads, and pivots from endpoint to instances to containers
- Provides response capabilities that allow you to contain and investigate compromised workloads and take action
- Includes CrowdScore™ Incident Workbench to unravel attacks and improve response time by distilling and correlating security alerts into incidents, automatically triaging, prioritizing and highlighting those that deserve urgent attention
Multi-Cloud Workload Discovery
Falcon provides visibility into the scope and nature of public and hybrid cloud footprints
- Automatically discovers existing cloud workload deployments - without installing an agent - by enumerating existing Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instances, Google Cloud Platform (GCP) Compute Engine instances and Microsoft Azure virtual machines
- Provides real-time information about workloads including context-rich metadata about system size and configuration, networking, and security group information for AWS, GCP and Azure
- Identifies workloads that are not protected by the Falcon platform
- Offers insight into your cloud footprint so you can secure all workloads, uncover and mitigate risks, and reduce the attack surface
Container Security
Falcon provides protection and visibility without impacting container performance.
- Secures the host and container via a single Falcon agent running on the host
- Investigates container incidents easily when detections are associated with the specific container and not bundled with the host events
- Captures container start, stop, image and runtime information, and all events generated inside the container even if it only runs for a few seconds
- Provides visibility into container footprint including on-premises and cloud deployments, and shows container usage, including trends, uptime, images used, and configuration to identify risky and misconfigured containers
- Offers a single management console for host and container security
Runtime Protection
The Falcon platform combines the best and latest technologies to protect against active attacks and threats when workloads are the most vulnerable - at runtime.
- Delivers machine learning (ML) and artificial intelligence (AI) to detect known and unknown malware
- Includes behavior-based indicators of attack (IOAs) that detect sophisticated threats such as fileless and malwarefree attacks
- Provides exploit protection
- Includes custom IOAs, whitelisting and blacklisting to tailor detection and prevention
- Offers integrated threat intelligence to block known malicious activities and deliver the complete context of an attack, including attribution
- Provides 24/7 managed threat hunting to ensure that stealthy attacks don't go undetected
API-Led Cloud Integration
Falcon eliminates friction to boost cloud security efficiency
- Powerful APIs allow automation of CrowdStrike Falcon functionality, including detection, management, response and intelligence
- Chef, Puppet and AWS Terraform integrations support continuous integration/continuous delivery (CI/ CD) deployment workflows
- Google Cloud Operating System (OS) configuration management integration automates Falcon agent deployment directly from GCP, without the need for custom scripts
- AWS PrivateLink integration enables sensor-to-cloud traffic to flow via PrivateLink, reducing internet exposure and simplifying network architectures
Simplicity and Performance
Built in the cloud for the cloud, Falcon reduces the overhead, friction and complexity associated with protecting cloud workloads
- One platform handles all workloads and works everywhere: private, public and hybrid clouds
- One console provides central visibility over cloud workloads, regardless of their location
- Falcon offers complete policy flexibility - apply at the individual workload, group or higher level
- It scales as cloud workloads expand - no need for additional infrastructure
- It operates with only a tiny footprint on the host and has almost zero impact on runtime performance, even when analyzing, searching and investigating
- Flexible consumption-based and annual-based subscription models support agile business planning
Documentation:
Download the CrowdStrike Falcon Cloud Workload Protection Datasheet (.PDF)

