
CrowdStrike Falcon Complete
Fully Managed Endpoint Protection Delivered as a Service by a CrowdStrike Team of Experts
CrowdStrike Falcon Complete
Contact us for Pricing!
Get a Quote
CrowdStrike Falcon Complete uniquely provides the technology, platform, actionable intelligence and skilled expertise required to provide comprehensive endpoint security from beginning to end. With Falcon Complete, customers can entrust the implementation, management and incident response of their endpoint security to CrowdStrike's proven team of security experts. The result is an instantly optimized security posture without the burden, overhead and cost of managing a comprehensive endpoint security program internally.
Overview:
Endpoint protection delivered as a service. The highest level of endpoint security maturity delivered immediately, without the burden of building and managing it yourself.
Falcon Complete - CrowdStrike Expertise and Technology, Your Security
CrowdStrike Falcon Complete uniquely provides the technology, platform, actionable intelligence and skilled expertise required to provide comprehensive endpoint security from beginning to end. With Falcon Complete, customers can entrust the implementation, management and incident response of their endpoint security to CrowdStrike’s proven team of security experts. The result is an instantly optimized security posture without the burden, overhead and cost of managing a comprehensive endpoint security program internally.
Built on the CrowdStrike Falcon platform, Falcon Complete is CrowdStrike’s most comprehensive endpoint protection solution. It provides unparalleled security by combining Falcon Prevent™ next-gen antivirus (NGAV), Falcon Insight™ endpoint detection and response (EDR) and Falcon OverWatch™ managed threat hunting with the expertise and 24/7 engagement of the CrowdStrike team. The team manages and actively monitors the Falcon platform for customers and remotely remediates incidents as needed. Falcon Complete combines the effectiveness of the Falcon platform with the efficiency of a dedicated team of security professionals, executing focused, incident-handling playbooks on your behalf.
Endpoint Security Delivered
Falcon Complete is the comprehensive endpoint security lifecycle solution that takes care of all aspects of endpoint security, including remotely remediating incidents with confidence, so you don’t have to. It allows you to gain the highest level of endpoint security while simplifying the implementation and day-to-day operations of your endpoint protection program. Falcon Complete uniquely provides the technology, platform, actionable intelligence and skilled expertise required to fully handle endpoint security, from beginning to end.
What makes Falcon Complete unique?
- Offloading Falcon endpoint protection to experienced CrowdStrike staff
- Assisting in deployment and configuration
- Providing 24x7 alert and incident handling
- Delivering proactive incident triage and containment
- Effectively handling incident remediation
- Ensuring transparent management reporting and metrics
Endpoint Protection As A Service
Fully managed endpoint protection delivered by CrowdStrike’s team of experts and the best endpoint security software in the industry - all backed by a guaranteed breach prevention warranty.
![]()
Achieves Instant Security Maturity
The Falcon Complete team instantly provides industry leading endpoint protection as a service 24/7.
![]()
Reduce Time to Remediate
Gain efficiency by reducing time to remediation - the Falcon Complete team are experts in remediation.
![]()
Improve Operation Effectiveness
You avoid the cost of having to hire, train, and retrain highly qualified FTE's - freeing up resources to be focused on other value-add activities.
Features:
Layers of Expertise
The Falcon Complete team is composed of seasoned security professionals with experience in incident handling, incident response, forensics, SOC analysis, identity protection and IT administration. The team has a global footprint, allowing true 24/7 coverage.
- Experts in the CrowdStrike Falcon platform: The Falcon Complete team holds CrowdStrike Certified Falcon Responder (CCFR) and CrowdStrike Certified Falcon Administrator (CCFA) certifications.
- Experts in incident response: The Falcon Complete team has years of experience in digital forensics and incident response (DFIR).
- Experts in threat hunting: The Falcon OverWatch team hunts and addresses undetected, sophisticated threats 24/7.
- Experts in threat intelligence: Falcon Complete is powered by the CrowdStrike global threat intelligence team, bringing critical context to the response process.


Powered by the Falcon Platform
CrowdStrike pioneered a new approach to endpoint protection, designed and built to overcome the limitations of legacy security solutions. The Falcon platform delivers the foundation for true next-generation endpoint protection.
- 100% cloud-native. The Falcon platform delivers immediate time-to-value - no hardware, additional software or configuration is required, which drives down cost and complexity.
- CrowdStrike Security Cloud. The CrowdStrike Security Cloud® is the brains behind the Falcon platform, providing complete real-time visibility and insight into everything happening on your endpoints throughout your environment.
- Single lightweight agent. The intelligent, lightweight Falcon agent, unlike any other, blocks attacks while capturing and recording endpoint activity as it happens to detect threats fast.
- Protection for endpoints, cloud workloads and identities. Enables frictionless endpoint, cloud workload and identity security, delivering real-time threat prevention and IT policy enforcement using identity, behavioral and risk analytics.
Proactive Management and Optimization
CrowdStrike experts ensure your environment is continuously optimized to combat the latest threats, achieving the best levels of performance and protection from your Falcon platform investment and ensuring confidence that your endpoint, cloud workload and identity protection are always under complete control.
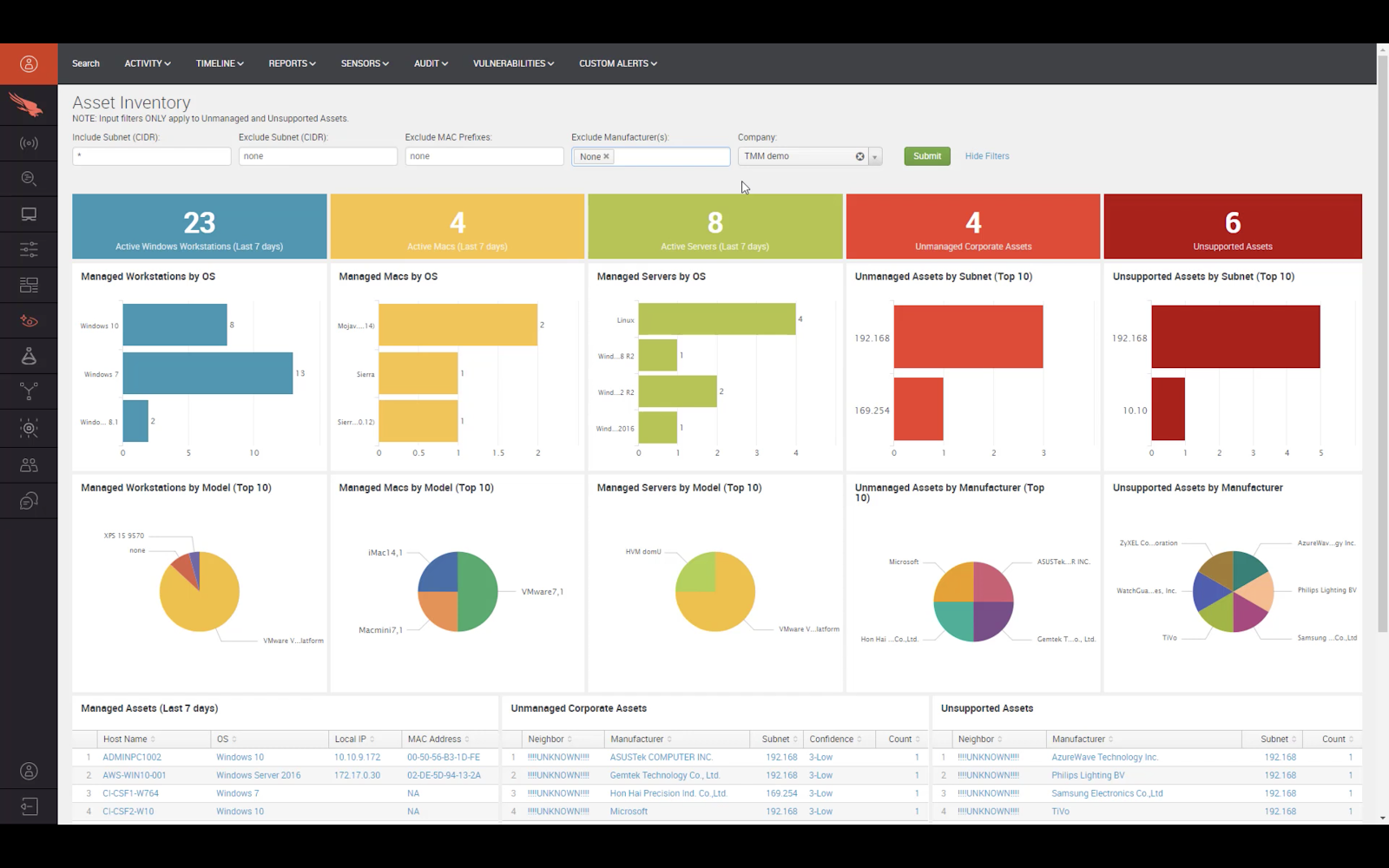
- Comprehensive control of unmanaged systems. Falcon Complete helps customers ensure all assets are properly grouped, sorted and protected.
- Tight control over the Falcon agent. Falcon Complete ensures that the current Falcon agent is installed, delivering the best level of protection available.
- Rigorous configuration management. Falcon Complete systematically applies proven, best-practice policies to endpoints and cloud workloads.

Continuous Human Threat Hunting
Falcon Complete includes 24/7 monitoring by the Falcon OverWatch team, CrowdStrike’s human threat detection engine that hunts relentlessly to see and stop the most sophisticated hidden threats.
- The SEARCH Methodology. Falcon OverWatch analysts leverage their proprietary SEARCH methodology - Sense, Enrich, Analyze, Reconstruct, Communicate and Hone - to shine a light into the darkest corners - leaving adversaries with nowhere to hide.
- Cloud-scale data. Scalable and effective threat hunting requires access to vast amounts of data and the ability to mine that data in real time for signs of intrusions. CrowdStrike’s rich telemetry creates the foundation for Falcon OverWatch threat hunting.
- Years of combined diverse expertise. Falcon OverWatch employs elite experts from a wide range of backgrounds, including government, law enforcement, commercial enterprise, the intelligence community and defense.
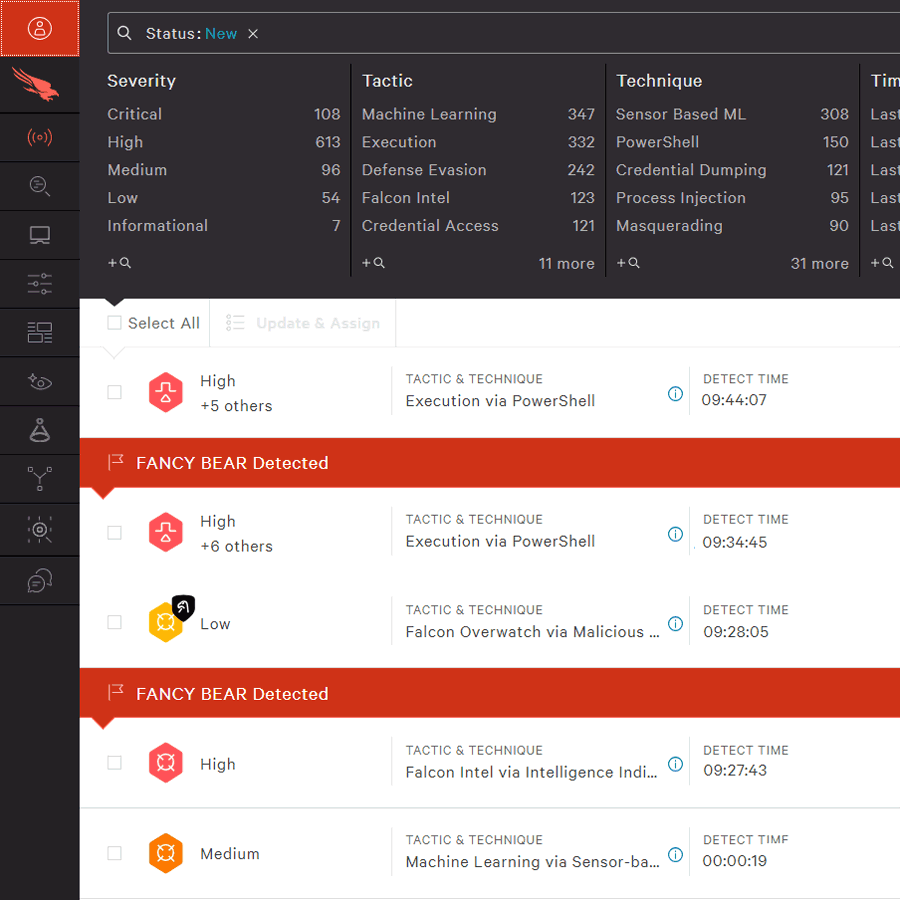
24/7 Monitoring and Response
The Falcon Complete team monitors your Falcon platform 24 hours a day, seven days a week, investigating every security alert with the goal of identifying potential intrusions at their very earliest stages.
- 24 hours/day active monitoring. Falcon Complete is always watching, ensuring that emerging threats are addressed in real time, as they happen.
- Human eyes on detections. Falcon Complete investigates the full spectrum of detections in a timely manner, ensuring that intrusions are identified at the earliest possible stage.
- <10 minutes: Average time to begin response. Falcon Complete builds and continuously tunes a repeatable playbook to ensure all threats are investigated quickly and efficiently.
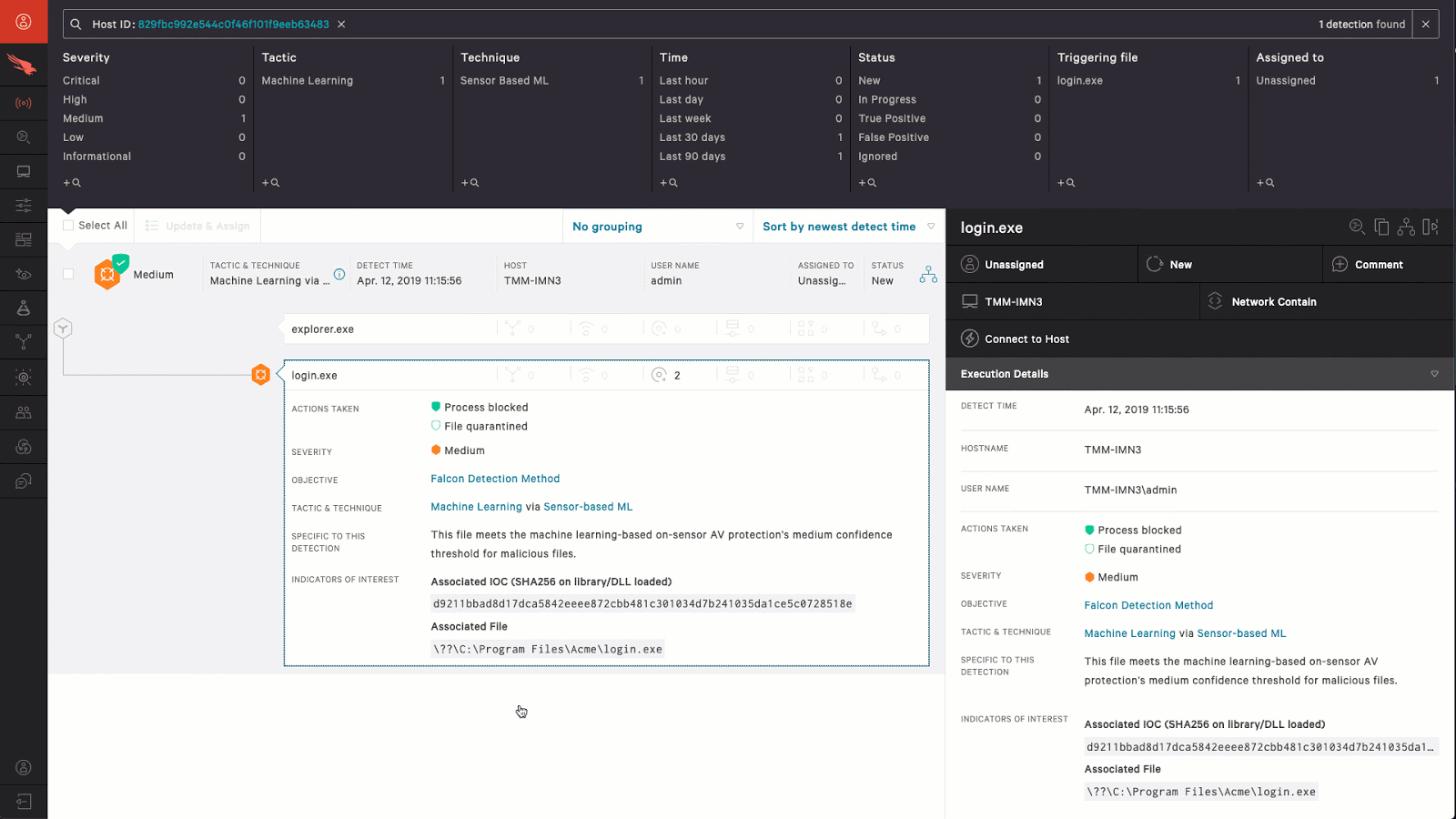
Surgical Remediation
When an intrusion is identified, the Falcon Complete team acts quickly and decisively, remotely accessing the affected system using native Falcon platform capabilities to surgically remove persistence mechanisms, stop active processes, block abuse of compromised accounts and clear other latent artifacts. Falcon Complete restores systems to their pre-intrusion state without the burden and disruption of reimaging systems.
- Surgical remediation in under 60 minutes. Falcon Complete executes surgical remediation remotely, eliminating the cost and burden of reimaging.
- Greatly reduced impact for the end user. Falcon Complete can often perform remediation without the user being aware that it has happened.
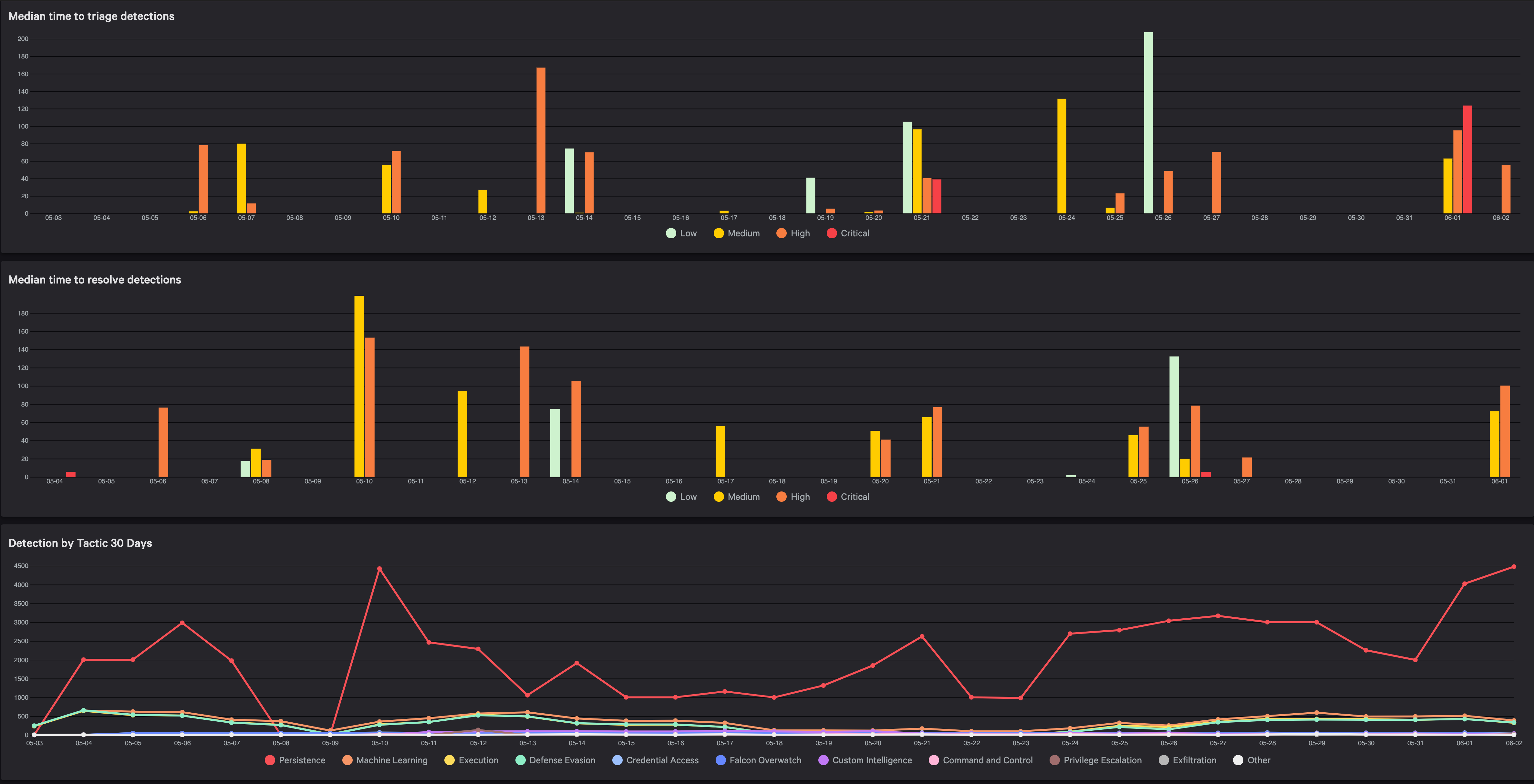
Transparent and Secure Collaboration
Falcon Complete delivers simple, transparent visibility and collaboration with CrowdStrike’s analysts ensuring you always have the information you need to make fast and effective decisions.
- Message Center: Provides secure bi-directional communication about emerging incidents as well as ad-hoc questions directly within the Falcon console. Keeping communications close to the Falcon data provides maximum efficiency, ensuring that the full context associated with emerging threats is never more than a click away.
- Executive Dashboards: Gain at-a-glance visibility into the day-to-day activity that Falcon Complete performs, including trends and actionable insights.
- Message Analyst: Fast access to CrowdStrike experts is embedded throughout the Falcon console. This helps analysts to more quickly understand threats, and get fast answers to their cybersecurity questions.

Breach Prevention Warranty
CrowdStrike stands strongly behind its breach protection capabilities. Falcon Complete comes with a Breach Prevention Warranty* to cover costs should a breach occur within the protected environment.
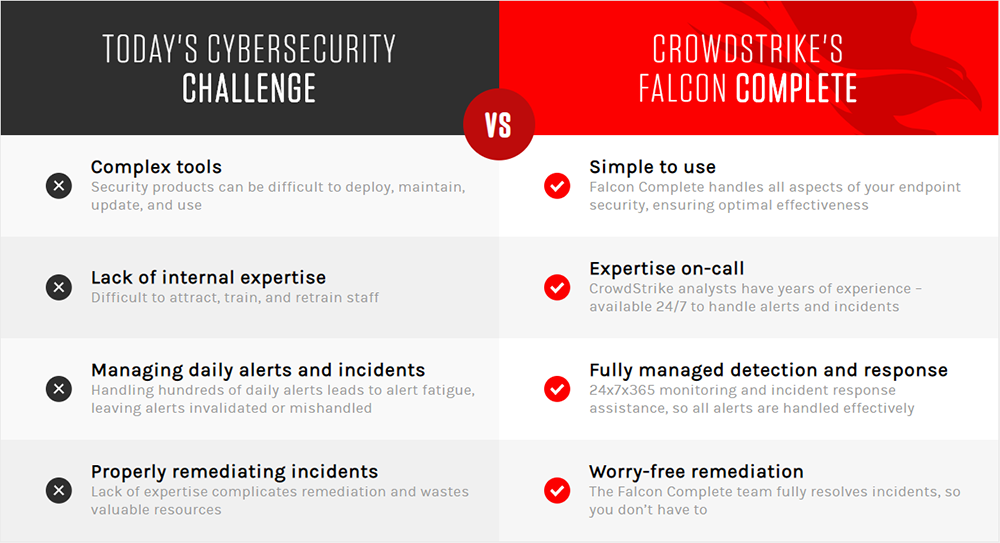
Cybersecurity Challenge:
Solves the challenge of managing, responding to and remediating threats
Operating an effective endpoint security program can be extremely challenging. The necessary tools can be difficult to use, requiring an abundance of resources to appropriately implement, support and maintain them over time. As a result, many organizations fail to get the most out of the endpoint security technologies they have acquired.
The situation is even worse for organizations that want to establish a strong endpoint security posture. Higher levels of security require even more resources as they can be costlier to maintain and more complex to manage.
The result? Many organizations do not successfully implement a fundamental endpoint security program, let alone a comprehensive one. The situation is exacerbated when serious incidents emerge and the organization does not have the time or expertise to properly remediate the situation, potentially endangering the safety of the organization.
There are some specific challenges that organizations can struggle with in their implementation of an endpoint security program:
- Difficulty fully implementing and properly configuring the technology they acquired: Depending on the size and workload of their IT teams, some organizations might not have the tools and bandwidth to quickly and successfully deploy the solution to their endpoints. In addition, they may lack the time and expertise needed to properly configure policies that match their security requirements and keep endpoints protected. This situation can result in an endpoint solution that is only partially deployed and poorly configured - resulting in gaps in protection that leave the organization vulnerable to breaches.
- Difficulty managing alerts and incidents day-to-day: Handling the potentially huge number of alerts generated by an endpoint security product can be overwhelming, even for organizations that have a dedicated security team or a SOC (security operation center). It not only takes manpower to manage alerts, it requires staff with enough cybersecurity expertise to understand the alerts and determine how to properly respond to them. Unfortunately, most organizations suffer from a shortage of both manpower and expertise, leaving alerts unvalidated and opening the door to high-profile breaches.
- Difficulty properly remediating incidents: The shortage of resources and expertise can lead organizations to struggle with understanding the nature and scope of an incident in a timely manner. This can mean incidents are not remediated efficiently, fully addressed, or handled in a timely manner, leaving organizations vulnerable or compromised. It takes skill and experience to know what to do to properly remediate an incident. Many organizations that lack resources are forced to go through the arduous process of reimaging endpoints, because the alternative of precisely combining countermeasures such as network containment, hash prevention, delete/modify registry key values or stop/disable/restart services is not possible. Yet, even reimaging does not ensure that the incident is fully remediated.
- Not having the budget to build a comprehensive endpoint security program: The cost of building a comprehensive security program that is staffed 24/7 by security experts is out of reach for many organizations, making the required level of security maturity unachievable for many companies.
- Time it takes to implement the program: Even if an organization possesses the financial means to build an internal endpoint security program, it can take a long time to implement a mature security strategy. From finding and hiring the right talent and acquiring the appropriate technology, to defining policies and creating an incident response (IR) process, the entire undertaking can take months if not years. In addition, such programs often are given a lower priority than other urgent IT projects, resulting in long implementation processes that leave organizations vulnerable.
- Difficulty finding and retaining the required expertise: It can be challenging for an organization to acquire the expert staff needed to efficiently secure their endpoints. For those who can afford it, recruiting, training and retaining the staff and skills to match an advanced and sophisticated threat landscape can be very difficult. This shortage of qualified expertise is an industry-wide problem.
- Some required components do not exist: Even if organizations decide to outsource their endpoint security, rather than build it internally, they will find that not all the necessary components can be easily found. One of the most difficult and sensitive steps is remediation. Most security providers will shy away from offering such a component because it requires a level of skill and experience they do not possess.
Modules Include:

Falcon Prevent
Next-gen AV
Protects against both malware and malware-free attacks; third-party tested and certified, allowing organizations to confidently replace their existing legacy AV

Falcon Insight
Endpoint Detection & Response
Delivers continuous and comprehensive endpoint visibility across detection, response and forensics, so nothing is missed and potential breaches can be stopped

Falcon Discover
IT Hygiene
Identifies unauthorised systems and applications, and alerts in real time to the use of privileged credentials in your environment, enabling faster remediation
Falcon Overwatch
Threat Hunting Service
Identifies attacks and stops breaches 24/7 with an elite team of experts who proactively hunt, investigate and advise on threat activity in your environment

Falcon Identity Threat Protection
Integrated Identity Security
Provides threat detection and real-time prevention of identity-based attacks.
Falcon Complete Team
Managed Detection & Response
Experienced analysts who manage, respond, and remediate alerts and incidents 24/7 - delivering endpoint protection as a a service using the Falcon Platform
Use Cases:
| Use Case: Difficulty Implementing Technology | Benefits | |
|---|---|---|
| Challenge | Depending on the size and workload of your IT teams, you may not have the tools and bandwidth necessary to quickly and fully implement endpoint security, leaving your organization vulnerable to breaches. | Falcon Complete handles all aspects of endpoint security, from deployment, configuration, maintenance and monitoring, to alert handling, incident response and remediation, ensuring you have effective endpoint security and reducing the risk of a breach. |
| Solution | Falcon Complete™ helps you successfully operationalize and optimize your endpoint security with:
|
|
| Use Case: Difficulty Managing Alerts and Incidents Day-To-Day | Benefits | |
| Challenge | Handling a large volume of alerts generated by an endpoint security product can be overwhelming. This can lead to alert fatigue and leave alerts invalidated or incorrectly handled, opening the door to breaches. | You benefit from 24x7x365 monitoring and incident handling assistance, ensuring that all alerts are effectively handled, reducing the risk of a serious breach. |
| Solution | Falcon Complete will manage all of these alerts and undertake the necessary actions:
|
|
| Use Case: Difficulty in Properly Remediating Incidents | Benefits | |
| Challenge | The Falcon Complete team will fully resolve the incident so that you don’t have to deal with it. |
|
| Solution | Falcon Complete will step in and undertake all of the actions needed to respond and remediate an incident:
|
|
Video:
Falcon Complete from CrowdStrike
CrowdStrike's Falcon Complete -- The highest level of endpoint security maturity delivered immediately, without the burden of building and managing it yourself.
Compare Falcon Endpoint Protection Solutions:
Support:
CrowdStrike offers premium support services to assist you with deployment and ongoing use of the CrowdStrike Falcon platform to ensure your success in keeping your environment secure and stopping breaches.
The CrowdStrike support organization is dedicated to resolving any issues quickly and effectively
CrowdStrike provides multiple levels of support so you can choose the level that best fits your organization’s requirements and ensures that you receive the most benefit from your investment in CrowdStrike.
CrowdStrike provides four levels of support:
Standard Support
Standard Support is bundled free with all Falcon subscriptions, providing basic support services, with a next-business-day response service level agreement (SLA).
Express Support
Express Support is designed for customers in small to medium-sized enterprise environments where deployment and operational issues must be addressed as quickly as possible.
Express Support provides everything included in Standard Support, plus:
- Prioritized case handling
- Quarterly health checks and reports
- Knowledge transfer opportunities
- Access to CrowdStrike’s team of technical account managers (TAMs) for product advice and issue escalation
- Enhanced knowledge base
- Premium video and webinar content
Essential Support
Essential Support is designed for mid-sized enterprise environments. From planning your deployment to ongoing operations, CrowdStrike’s team of support professionals understands the importance of your mission and are committed to working with you to avoid problems and resolve issues as quickly as possible.
Companies that value proactive engagement to avoid issues and fast and predictable access to support will benefit from this service.
Essential Support provides everything included in Express Support, plus:
- 30 days of personalized onboarding support
- Invitations to Beta Programs
- Periodic proactive calls from a TAM
- Reports covering the overall health of your CrowdStrike deployment, best practices, tuning, case status and reviews of new product features and capabilities
Elite Support
Elite Support is the highest level of support provided by CrowdStrike. A named TAM works closely with you as an extension of your team.
Elite Support builds on CrowdStrike Essential Support and adds the following:
- Custom reporting
- Weekly scheduled meetings
- On-site visits (up to quarterly)
- Product management team access
- Named TAM
| Support Level | Standard | Express | Essential | Elite |
|---|---|---|---|---|
| Support Access | ||||
| Support Portal (Knowledge Base, Case Submissions) | ||||
| 24/7/365 Phone Support for Emergencies | ||||
| Live Chat (Business Hours) | ||||
| Priority Case Assignment | ||||
| Premium Support Content (Articles, Videos, Webinars) | ||||
| Access to TAM Team for Product Advice and Escalations | ||||
| Named TAM | ||||
| Technical Account Management | ||||
| Proactive Case Management | ||||
| Quarterly Reports | Custom | |||
| Weekly Deployment Follow-up Meetings | ||||
| Proactive Outreach | ||||
| Quarterly Health Checks | ||||
| Beta Program Invitations | ||||
| Roadmap Webinars | ||||
| On-site Visits | ||||
| Ad-hoc Product Guidance and Knowledge Transfer | ||||
| First 30 Days Ramp-Up | ||||
| Welcome Letter | ||||
| 1:1 Quick Start Call | ||||
| Weekly and Monthly Premium Support Newsletters | ||||
| Onboarding Webinar | ||||
Support Care
Response Time
- Standard: The support engineer responds to technical issues within one business day of a call or one business hour for critical issues.
- Express, Essential: The support engineer responds to technical issues within four business hours of a call or one business hour for critical issues.
- Elite: The support engineer responds to technical issues within four business hours of a call or one business hour for critical issues.
24x7 Critical Issue Support
- Standard: For critical technical issues (P1 - Network down), the support team is available around the clock.
- Express, Essential and Elite: For critical technical issues, the team will be available around the clock, escalating issues as appropriate for the quickest possible resolution. You will be given a dedicated phone number for these critical cases.
Prioritized Case Handling
- Express, Essential and Elite Support cases take precedence over Standard cases at the same priority level.
Proactive Support
- Essential and Elite: During periodic calls scheduled at your convenience, a member of the TAM team will provide Q&A or just-in-time training on topics of your choice, updates on the latest product features, and general platform health checks.
Product Care
Defect Handling
- Standard: When determined the issue could be caused by a defect in the product, a case will be opened on the customer’s behalf and managed to resolution.
- Express, Essential and Elite: When determined the issue could be caused by a defect in the product, the customer’s ticket will take precedence over others within the same priority level.
Feature Requests
Feature requests should be submitted through the Ideas section in the Falcon Support Portal where they are regularly reviewed and prioritized by the product teams.
Account Care
Technical Account Manager Team
- Express, Essential and Elite: You receive direct access to the TAM team, which will be your liaison to support and product management.
Documentation:
Download the CrowdStrike Falcon Endpoint Protection Complete Datasheet (.PDF)
Download the CrowdStrike Falcon Support Datasheet (.PDF)









