
CrowdStrike Falcon X Recon+
Digital Risk Protection
Falcon X Recon+: Digital Risk Protection
Falcon X Recon+ simplifies the process of hunting for external threats to brands, employees and sensitive data on the open, deep and dark web.
Managed Threat Monitoring for the Open, Deep and Dark Web
CrowdStrike experts manage the effort of monitoring, triaging, assessing and mitigating threats across the criminal underground so you can focus on your business. Our experts monitor, on your behalf, data from restricted forums, marketplaces, messaging platforms, social media posts, data leak sites and much more to provide relevant, real-time warnings and identify data exposure and threats to your business.
Falcon X Recon+ threat experts assess and recommend effective mitigation steps, enabling you to act decisively with proactive steps to prevent and detect future attacks. The mitigation steps may include CrowdStrike facilitating the process of taking down malicious content that may threaten your brand or reputation, such as deleting harmful social media posts, removing data from paste sites, and removing spoofed or impersonated domains.
By offloading this effort to CrowdStrike, Falcon X Recon+ increases the effectiveness of your security team, while reducing the time, skills and effort required to battle sophisticated adversaries.
Benefits
Includes everything in Falcon X Recon, but CrowdStrike manage it for you.
Cybercrime Monitoring
Falcon X Recon+ includes the technology required to deliver near real-time visibility across the vast cybercriminal underground and the skills to manage the system for you.
Deep Expertise
Falcon X Recon+ provides direct access to a CrowdStrike expert with proven effectiveness in identifying and mitigating threats across the criminal underground.
Rapid Takedowns
CrowdStrike helps facilitate the takedown of fraudulent accounts, phishing websites, domains, and malicious posts that can potentially harm your business.
Collect
Falcon X Recon provides instant access to over eight years of data from difficult-to-access digital channels of the open, deep and dark web. Falcon X Recon proactively collects raw intelligence about fraudulent activity, stolen data, threats to enterprises, and identified exploits and tools in the adversaries’ arsenals.
- Collect raw intelligence at scale: Automatically monitor data from millions of hidden web pages and thousands of restricted forums, marketplaces, paste sites, IRC channels, rogue apps, phishing domains, and open and closed messaging applications like Telegram, QQ and more.
- Perform real-time, covert investigations: Disrupt adversaries with access to real-time raw intelligence, and limit their opportunities to attack. Perform investigations with undetectable access to data from restricted sites. Falcon X Recon stores historical data so adversaries can’t cover their tracks by changing or deleting posts.
- Track criminal adversaries: Analyze and track attacker behavioral changes over time, and identify increases in activity, emerging attacks, new targets, and evolving tradecraft and tools, so you can better protect against external threats.
Investigate
Gain real-time visibility to potential threats, and accelerate investigations into fraudulent activity targeting your organization. Falcon X Recon eliminates risky guesswork and enriches traditional incident response by providing broader context to improve the depth and breadth of investigative reporting and analysis.
- Identify targeted threats: Continuously monitor underground environments for external threats to the organization without the need for creating complex queries. Falcon X Recon provides easy-to-use wizards that include predefined search criteria, like brand names, executives, domains, vulnerabilities, email addresses and many more. Create and save your own monitoring rules to proactively sift through raw intelligence or share them with your team.
- Expose the adversary: Investigate results displayed in customizable dashboards and easy-to-read cards. Users can view the original threat actor posts with additional context about the actor and the site. Results are viewed in their original language and can be translated from 18 other languages using augmented translation with hacker slang dictionaries.
- Enrich investigations: Gain a complete understanding of the threat. Universal Search enables users to automatically correlate Falcon X Recon results with additional context provided by other licensed CrowdStrike Falcon modules. Maximize efficiency and effectiveness of response by revealing the relationships between digital threats and endpoint detections, hosts, threat intelligence reports, vulnerabilities and much more.
Notify
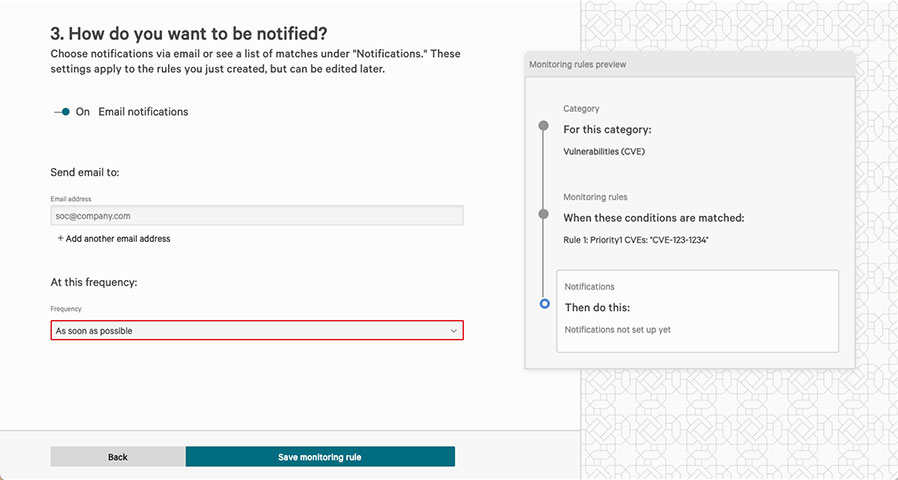
Optimize the investigation and response workflow with real-time notifications when potential threats are identified. Ensure that the users responsible for triage and response have the details they need at their fingertips.
- Prioritize alerts: Set the priority of the alert based on the criticality of the external threat. Immediately pivot from the notification to the details of the alert.
- Gain complete administrative control: Customize how team members are notified and how often they receive alerts. They can be alerted immediately or on a schedule such as daily or weekly. Toggle notifications on or off without affecting the underlying monitoring rule.
- Inform the right team: Go beyond cybersecurity - digital threats affect an organization’s brand, reputation and employee safety. Alert your departments outside of security, such as marketing, legal, human resources and fraud.
Deep Expertise
- Falcon X Recon+ provides direct access to a CrowdStrike expert with proven effectiveness in identifying and mitigating threats across the criminal underground.
- CrowdStrike experts continuously hunt for potential external threats to your organization, keeping you updated on verified threats and eliminating the noise.
- Receive threat assessments with proactive steps to prevent and detect future threats.
Unrivaled Coverage
- Gain near real-time visibility into potential external threats across millions of hidden web pages and restricted sites on the open, deep and dark web.
- Keep pace with the vast and dynamic underground - CrowdStrike updates monitoring rules to identify emerging threats to your business.
Takedown Facilitation
- CrowdStrike works on your behalf to identify and facilitate the takedown of fraudulent accounts, phishing websites, domains and malicious posts that can harm your reputation or business.
- Save time by letting CrowdStrike facilitate the costly process of reporting to the host provider to remove the malicious content quickly and effectively before there is damage to your brand or business reputation.
Falcon X Recon Offerings
Choose the option that suits you best

Falcon X Recon
Falcon X Recon enables security teams to monitor and track adversaries across the open, deep and dark web.

Falcon X Recon+
Includes everything in Falcon X Recon, but CrowdStrike manages it for you. Falcon X Recon+ reduces the time, skills and effort required for you to battle sophisticated adversaries.
Falcon X Recon |
Falcon X Recon+ |
|
|---|---|---|
| Access Data from the Open, Deep, and Dark Web | ||
| Create Monitoring Rules | ||
| Set and Manage Alerts | ||
| Universal Search | ||
| Actor Profiles and Indicator Feed | ||
| Assigned CrownStrike Expert |
||
| Managed Rule Monitoring | ||
| Alert Triage and Assessment | ||
| Mitigation Recommendations | ||
| Updates and Threat Briefing | ||
| Takedown Service |
Documentation:
Download the CrowdStrike Falcon X Recon+ Datasheet (.PDF)

