
CrowdStrike Falcon XDR
Extend Beyond The Endpoint
Falcon XDR: Extend Beyond The Endpoint
Supercharge detection and response across your security stack with Falcon XDR. With industry-leading endpoint protection at its core, Falcon XDR synthesizes multi-domain telemetry to provide security teams with one unified, threat-centric command console.
Challenges
Today, many organizations rely on a collection of disparate security tools to identify and mitigate threats. These siloed security implementations are inherently inefficient and ineffective. Detecting, isolating and remediating security incidents is resource-intensive, time-consuming and error-prone, and involves multiple platforms and administrative interfaces. To get to the bottom of an issue, security analysts are often forced to manually sift through and piece together volumes of diverse alert and event data generated by different systems.
To make matters worse, today’s sophisticated threat actors know where to look for gaps in security silos. They can slip between defenses and move laterally across the network, flying under the radar for extended periods of time, lying in wait and gathering reconnaissance data for future attacks.
For more effective protection, organizations need to optimize real-time threat detection, investigation and hunting across environments and domains. They need extended detection and response (XDR).
Solution
Falcon XDR extends CrowdStrike’s industry-leading endpoint detection and response (EDR) capabilities and delivers real-time multi-domain detection and orchestrated response to improve threat visibility across the enterprise, accelerate security operations and reduce risk. The CrowdStrike Security Cloud correlates trillions of security events per day with indicators of attack, the industry’s leading threat intelligence, and enterprise telemetry from across customer endpoints, workloads, identities, DevOps, IT assets and configurations. Falcon XDR seamlessly adds third-party telemetry from a wide range of security solutions to this threat-centric data fabric, powering the next generation of detection, protection and elite threat hunting to stop breaches faster.
Key Benefits of Choosing Falcon XDR

EXTENDED
Take EDR to the next level with consolidated, multi-platform telemetry that dramatically enhances threat correlation and speeds response times against sophisticated attacks.

DETECTION
Accelerate threat analysis and hunting by transforming previously siloed, disconnected data into strong, cross-platform attack indicators, insights, and alerts.

RESPONSE
Turn XDR insight into orchestrated action. Empower security teams to design and automate multi-stage, multi-platform response workflows for surgical, full-stack remediation.
Optimize Security Operations
With the industry's leading EDR at the core, take your team to the next level with the power of Falcon XDR
- Create a cohesive, more effective cybersecurity stack: Surface actionable insights when previously siloed data comes together into one single source of security truth.
- Aggregate disparate threat data on a massive scale - with ease: Purpose-built XDR integrations and an open data schema streamline telemetry ingestion, parsing and mapping to provide unmatched visibility across the entire environment.
- Maximize time and effort: Advanced Falcon XDR analytics automatically detect stealthy threats, eliminating the need for you or a number of people on your team to write, tune and maintain detection rules.
Get The Right Answers, Fast
Accelerate multi-domain threat analysis, investigation and hunting from a single console
- Explore live, fast-moving threats like never before: Search index-free across structured and unstructured data from any XDR source to accelerate cross-domain threat hunting and investigation.
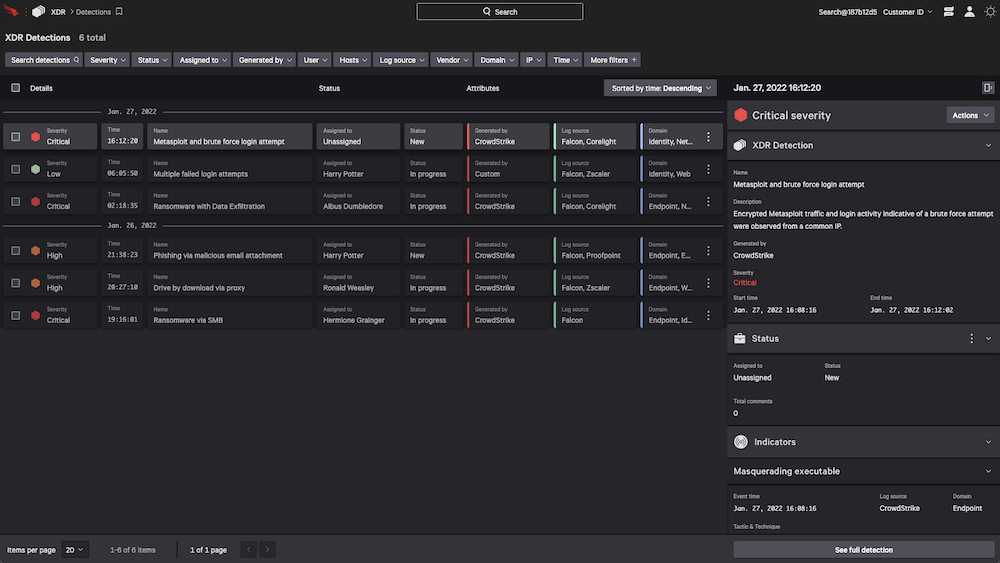
- Speed triage and investigation: Prioritized alerts, rich context, and detailed detection information mapped to the MITRE ATT&CK framework help analysts quickly understand and act on threats. The intuitive Falcon console lets you quickly tailor views, filter and pivot across data sets with ease.
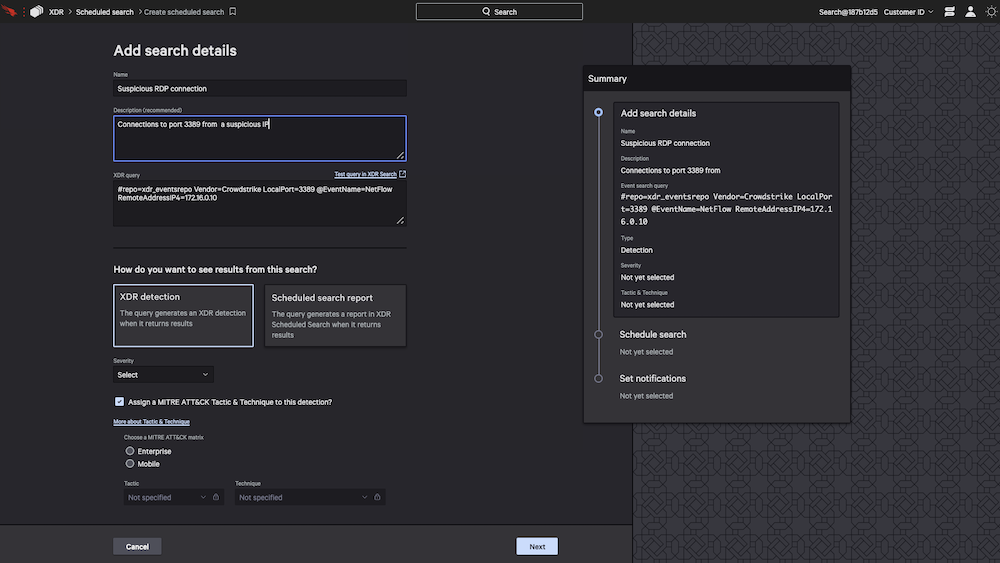
- Schedule searches and create custom detections: Build custom scheduled queries and detections for behaviors and activity unique to your organization.
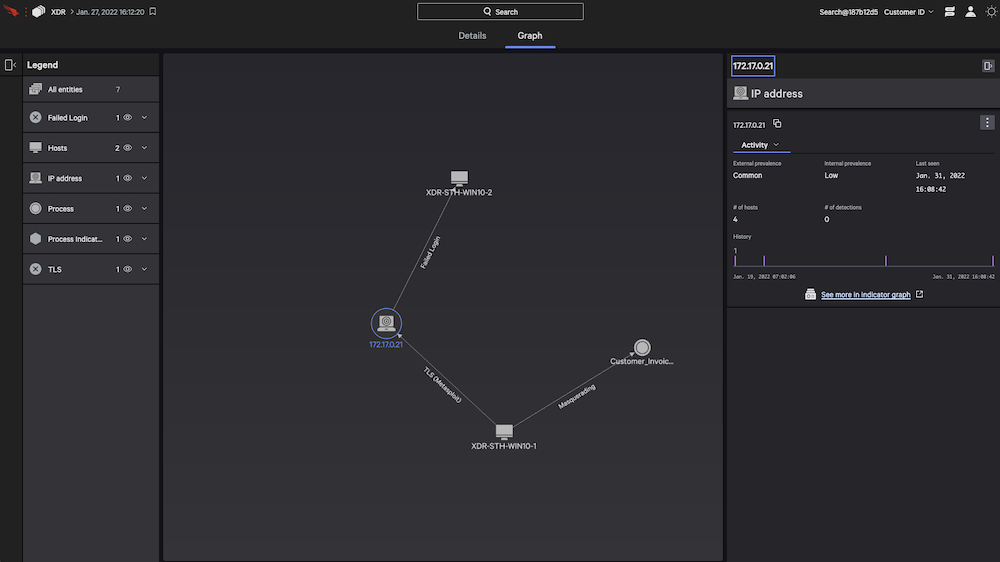
- View the entire cross-domain attack: The interactive graph explorer visualizes each step of an attack for quick understanding.
Stop Attacks Before They Become Breaches
Speed response times and orchestrate action against sophisticated attacks
- Respond decisively: Detailed detection information - from impacted hosts and root cause to indicators and timelines - guides remediation. Powerful response actions allow you to eradicate threats with surgical precision.
- Quickly move investigation to action: Contain hosts associated with suspicious activity instantly - right from the detection.
- Orchestrate and automate workflows: Falcon Fusion streamlines tasks - from notifications and repetitive tasks to complex workflows - dramatically improving the efficiency of your SOC teams.
Why Organizations Need XDR: 3 Benefits of XDR Security
XDR coordinates and extends the value of siloed security tools, unifying and streamlining security analysis, investigation and remediation. As a result, XDR provides the following benefits:
- Consolidated threat visibility: XDR delivers granular visibility by working across multiple layers, collecting and correlating data from email, endpoints, servers, cloud workloads and networks.
- Hassle-free detections and investigation: Analysts and threat hunters can focus on high-priority threats because XDR weeds out anomalies determined to be insignificant from the alert stream. And with advanced analytics and correlation content prebuilt in the tool, XDR automatically detects stealthy threats - all but eliminating the need for security teams to spend time constantly writing, tuning, and managing detection rules.
- End-to-end orchestration and response: Detailed, cross-domain threat context and telemetry - from impacted hosts and root cause to indicators and timelines - guides the entire investigation and remediation process. Automated alerts and powerful response actions can trigger complex, multi-tool workflows for dramatic SOC efficiency gains and surgical threat neutralization.
XDR vs Other Detection and Response Technologies
XDR often gets confused with similar “detect and respond” acronyms that make up the alphabet soup of cybersecurity technology. Below is a quick explanation of the differences between XDR and other detection and response technologies:
- Endpoint detection and response (EDR): Monitors end-user devices - desktops, laptops, tablets and phones - for threats that antivirus software can't detect
- Managed Detection and Response (MDR): Essentially EDR purchased as a service.
- Network Detection and Response (NDR): Monitors communications within the network to detect, investigate and respond to threats that might otherwise remain hidden in unmanaged devices across on-premises, cloud and hybrid environments.
- Identity Threat Detection and Response (ITDR): Detects threats to all Service and Privileged accounts on your network and cloud.
- Extended Detection and Response (XDR): Uses EDR capabilities to extend protection beyond endpoints to also monitor data from networks, cloud workloads, servers, email, and more.
The Evolution of EDR
XDR is the evolution of EDR. In a recent Forrester report, analyst Allie Mellen explained that, "good XDR lives and dies by the foundation of a good EDR." If you don't start with the endpoint, there's nothing for XDR to "extend."
XDR builds on the core functions of EDR and makes all telemetry accessible - from endpoints, cloud workloads, identity, email, network traffic, virtual containers, sensors (from operational technology, or OT) and more.
Is XDR the Same as SIEM?
No. XDR isn't about aggregation, it's about results.
XDR makes real-time threat detection easier by bringing together world-class threat hunting, machine learning (ML), artificial intelligence (AI) and threat intelligence with third-party data sources. Unlike SIEM, XDR delivers impactful remediation strategies by intelligently consolidating all of the valuable telemetry from security solutions, while also orchestrating and automating analysis.
How XDR Works
XDR connects data from siloed security solutions so they can work together to improve threat visibility and reduce the length of time required to identify and respond to an attack. XDR enables advanced forensic investigation and threat hunting capabilities across multiple domains from a single console.
Here’s a simple step-by-step of how XDR works:
- Step 1. Ingest: Ingest and normalize volumes of data from endpoints, cloud workloads, identity, email, network traffic, virtual containers and more.
- Step 2. Detect: Parse and correlate data to automatically detect stealthy threats with advanced artificial intelligence (AI) and machine learning (ML).
- Step 3. Respond: Prioritize threat data by severity so that threat hunters can quickly analyze and triage new events, and automate investigation and response activities.

Key XDR Requirements
To fully deliver on its promise for optimum detection, investigation, hunting and incident response, any XDR solution you are considering must demonstrate the following requirements:
- Runs on a cloud-native platform. It operates at sufficient scale, with the ability to ingest data from multiple sources, provides broad visibility and detection capabilities across all data, and is positioned to orchestrate automated response.
- Extends endpoint security. It continues to focus protection on endpoints but extends visibility, detection and response beyond them through best-of-breed integrations with security solutions through an open data scheme.
- Focuses on threats. It automatically detects stealthy threats, eliminating the need to write, tune and maintain detection rules.
- Offers broad, relevant and enriched telemetry. It incorporates a broad, diverse set of systems and applications for more comprehensive contextualization and correlation, including network analysis and visibility (NAV), next-generation firewall (NGFW), email security, identity and access management (IAM), cloud workload protection (CWP), cloud access security broker (CASB) and others.
- Communicates with security tools. It leverages open, well-defined schemas for data exchanges with additional IT security systems to ensure enrichment and correlation take place in a consistent and comprehensive fashion with key objectives and outcomes in mind.
- Ensures investigations are meaningful. It emphasizes data fidelity and detection quality to ensure XDR events and investigations are meaningful and efficient, minimizing false positives.
- Expedites response. With multistage, multiplatform response workflows, it enables security teams to take swift - even automated - action to mitigate and remediate threats detected.
- Continues to search for unknowns. Applies advanced security analytics, AI and ML to continuously search for previously hidden threats using aggregation and understanding of multiple, disparate weaker signals from different security domains across the security stack.
Falcon XDR: CrowdStrike's XDR Solution
Falcon XDR unifies detection and response across your security stack to take CrowdStrike's EDR technologies to the next level. Falcon and non-Falcon telemetry are integrated into one single command console for unified detection and response. Falcon XDR turns cryptic signals trapped in siloed solutions into high-efficacy, real-time detections and deep investigation context. Equipped with Falcon XDR, security professionals can more quickly and intuitively investigate, threat hunt and respond.
Documentation:
Download the CrowdStrike Falcon XDR Datasheet (.PDF)

